Palo Alto Training – Learn Palo Alto Firewalls in 2025

Session fixation attacks are a cunning session hijacking technique that exploit session ID exploitation to take over user logins. By tricking victims into using a pre-set session ID via a cookie fixation vulnerability, attackers gain unauthorized access once the user authenticates. This web session vulnerability leverages a session management flaw, often turning it into an authentication bypass attack. Recognized in the session fixation OWASP guidelines, it threatens […]
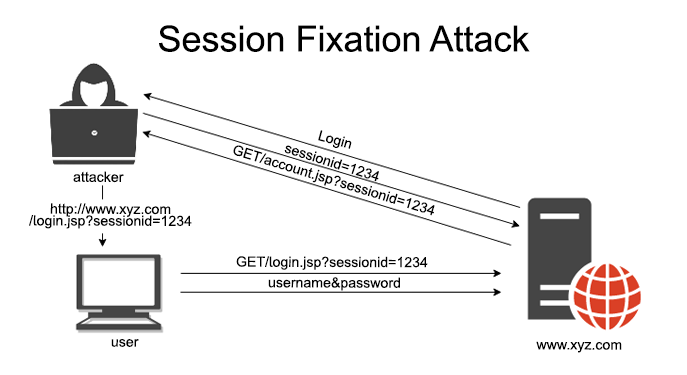
Session fixation attacks are a cunning session hijacking technique that exploit session ID exploitation to take over user logins. By tricking victims into using a pre-set session ID via a cookie fixation vulnerability, attackers gain unauthorized access once the user authenticates. This web session vulnerability leverages a session management flaw, often turning it into an authentication bypass attack. Recognized in the session fixation OWASP guidelines, it threatens platforms like session fixation in PHP, session fixation in Java, and session fixation in Node.js. In 2025, as web apps proliferate, understanding session token manipulation and HTTP session attack risks is vital. This article explores session fixation examples, real-world cases, and session fixation prevention strategies to secure your applications.
A session fixation attack thrives on poor secure session management, allowing attackers to hijack active sessions without stealing credentials directly. Unlike session fixation vs session hijacking, where hijacking snags an existing session, fixation pre-emptively sets the trap. By exploiting a cookie fixation vulnerability, an attacker can force a user to inherit a known session ID, then wait for login to piggyback on it. This session management flaw is insidious in session fixation in ASP.NET or any framework neglecting session regeneration best practices. For businesses, it risks account takeovers; for developers, it’s a wake-up call to enforce session fixation mitigation.
Here’s how session token manipulation powers this attack, with practical insights:
A session fixation real-world case: In 2010, a banking app’s failure to regenerate session IDs let attackers hijack accounts via phishing links. Tools like Burp Suite aid session fixation detection. Pricing Section: In 2025, certifications to master this include: CEH (2,000 € – 2,500 €), OSCP (2,100 € – 2,500 €), WAHS (500 € – 1,500 €), CISSP (800 € – 1,200 €), CompTIA Security+ (350 € – 400 €). WAHS covers session fixation in ASP.NET, while OSCP dives into session fixation defense patterns.
Session fixation prevention hinges on robust secure session management. Here’s how to protect your systems:
For more, see Wikipedia or Gartner. The University of Rennes 1 offers relevant training.
Session fixation attacks hijack logins via session hijacking techniques, exploiting web session vulnerabilities from session fixation in PHP to session fixation in Java. With session token manipulation and authentication bypass attacks, this session fixation OWASP-listed threat demands action. Real-world breaches underscore the need for session fixation defense patterns. Certifications like WAHS and OSCP equip you with secure session management skills. Explore cybersecurity certification training at SecureValley Training Center to safeguard your users today!
Get certified with industry-leading cybersecurity certifications from EC-Council, PECB, Palo Alto Networks, and more.

Learn from world-class instructors Collaborate with top professionals Advanced training...

The CEH is the world's leading cybersecurity certification, recognized by...

Onsite training course Led by an instructor Interactive sessions

Asynchronous, self-study environment Video-streaming format Flexible learning schedule
Adding {{itemName}} to cart
Added {{itemName}} to cart

