Palo Alto Training – Learn Palo Alto Firewalls in 2025

CSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions CSRF (Cross-Site Request Forgery): How Hackers Hijack Sessions CSRF attacks, or Cross-Site Request Forgery, are stealthy web security vulnerabilities that enable hackers to perform session hijacking by tricking users into executing unwanted actions on trusted sites. This article explores the CSRF vulnerability, how attackers craft a CSRF […]
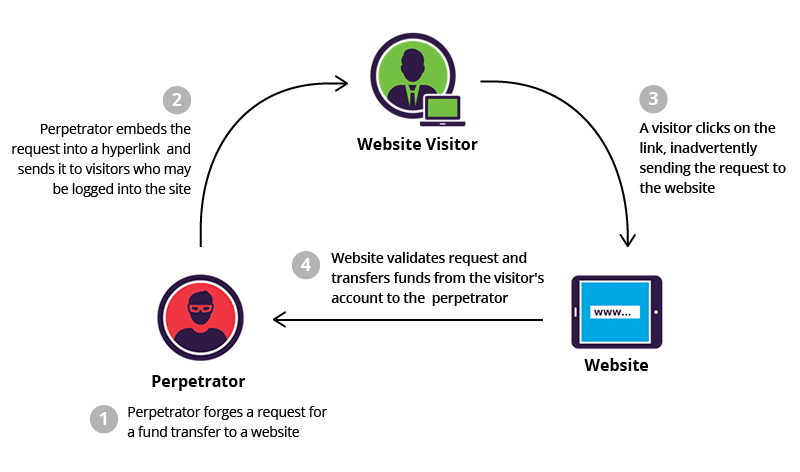
CSRF attacks, or Cross-Site Request Forgery, are stealthy web security vulnerabilities that enable hackers to perform session hijacking by tricking users into executing unwanted actions on trusted sites. This article explores the CSRF vulnerability, how attackers craft a CSRF exploit, and effective CSRF protection methods like CSRF tokens. With CSRF examples and real-world CSRF cases, we’ll uncover why OWASP CSRF ranks it as a top threat and how to prevent CSRF attacks in 2025, even in CSRF in APIs and CSRF in modern frameworks.
A CSRF attack occurs when a malicious site tricks a user’s browser into sending unauthorized state-changing request attacks to a trusted site where the user is authenticated. For example, if a user is logged into their bank and visits a malicious page, a hidden form might silently submit a transfer request like <form action="https://bank.com/transfer" method="POST"><input type="hidden" name="amount" value="1000"></form>. The browser, unaware, sends the request with the user’s session cookies, executing the action. This CSRF vs XSS distinction is key: unlike XSS, CSRF doesn’t steal data directly but hijacks actions, exploiting browser security issues.
Hackers use CSRF payloads to craft exploits, often embedding them in phishing emails, malicious websites, or compromised ads. A CSRF attack demonstration might involve an image tag like <img src="https://bank.com/transfer?amount=1000&to=attacker"> that triggers a GET request when loaded. More advanced CSRF exploits use POST requests via auto-submitting forms. Real-world CSRF cases include the 2008 Netflix attack, where attackers changed user settings without consent. CSRF testing with tools like Burp Suite helps identify these CSRF vulnerabilities in apps.
CSRF mitigation relies on robust defenses:
<input type="hidden" name="csrf_token" value="random123">), verified server-side to block unauthorized requests.SameSite=Strict to limit cross-origin requests, a key CSRF best practice.CSRF secure coding also includes checking HTTP methods (e.g., rejecting GET for state changes) and securing CSRF in APIs with token-based authentication. A CSRF prevention checklist ensures comprehensive coverage across CSRF in modern frameworks like React or Angular.
Cross-Site Request Forgery remains a potent threat, hijacking sessions via deceptive CSRF attacks. From a simple CSRF example like a hidden form to complex CSRF payloads, understanding this vulnerability is vital. CSRF protection with anti-CSRF tokens and CSRF best practices can thwart these exploits. For hands-on skills, explore the WAHS certification at SecureValley Training Center, or check our program at WAHS. Secure your web apps now!
For more info, visit Wikipedia, University of Rennes, or Gartner.
Get certified with industry-leading cybersecurity certifications from EC-Council, PECB, Palo Alto Networks, and more.

Learn from world-class instructors Collaborate with top professionals Advanced training...

The CEH is the world's leading cybersecurity certification, recognized by...

Onsite training course Led by an instructor Interactive sessions

Asynchronous, self-study environment Video-streaming format Flexible learning schedule
Adding {{itemName}} to cart
Added {{itemName}} to cart

